Account Policies
Account policies are a set of security rules that you can apply to a user. You can create multiple policies, but only one policy may be enforced for any one user at a time. A default policy exists, but you are likely to want to create additional policies that you can use as a template against which different user may be applied.
To Add a New Account Policy in Security Server:
-
Open the Workbench, then expand the current project to show the Security provider node, and then expand to show the Policies node as shown below.
- Right-click Policies
and select Add Policy or select this function from the Workbench Home tab. This displays the Account Policy
form which has two tabs: an Account Policy tab and a Time
Sheet tab.
Password Recommendations
Using the Account Policy form, you specify how passwords must be used, and whether users are automatically locked out after a series of incorrect login attempts. You can use these settings to make your passwords harder to crack, set auto logout policy, and determine how to handle failed login attempts. Users with access to sensitive data should be subjected to more stringent policies than users who access non-sensitive data. The following policies are recommended for access to sensitive data:
- Enforce a change of passwords by a user after no less than 30 days; less for more sensitive data access.
- Lock the account after 3 or 4 failed logins, and force the locked out user to contact an
- Set a reasonable logout time so that if a user leaves their console unattended, that the system cannot be compromised. The interval can be changed in the Auto Logout after combo box.
- Enforce password lengths and complexity. A password of 6 characters or more with mixed characters (alpha and numeric) is considered to be the minimum required to defeat brute force attacks.
Refer to Logins and Passwords for more information.
The Default Account Policy
The base policy (i.e., the most restrictive) for the system is set in
the default policy. This is the first account policy defined in GENESIS64,
and by default it is called "Default Policy". You can define
other policies but each user account subscribes to one and only
one account policy. For example, you might have one account policy
for for administrators and another for a category of users, such as General Operators which includes some restrictions accessing information during GraphWorX64 Runtime. ![]() View image
View image
 Account Policies specifies the standard password log in and log out for the account. See Global Settings for security authorization to access GENESIS64 applications and assigning the authorization roles for users and groups of users. See Users
and Groups to establish individual and the group security privileges.
Account Policies specifies the standard password log in and log out for the account. See Global Settings for security authorization to access GENESIS64 applications and assigning the authorization roles for users and groups of users. See Users
and Groups to establish individual and the group security privileges.
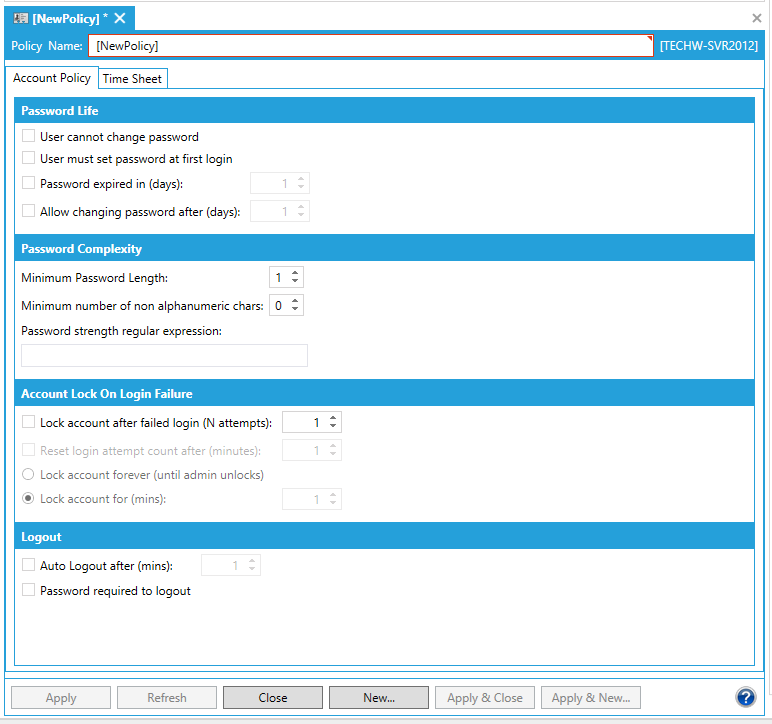
Account Policy Tab
The five sections on the Account Policy tab are very similar to the ones you would see in a Windows domain-based policy for a user account. The table below details the different options and their descriptions for the Account Policy tab.
|
Password Life Properties |
Description |
|---|---|
|
User cannot change password |
If selected, the password can only be changed by an Administrator when enabled. |
|
User must set password at first login |
If selected, forces the user to change the default password that the account starts with. This can be triggered by password expiration. The user will receive a message when the password is going to expire. |
|
Password expires in (days) |
If selected, users must create a new password after a password has been used for the number of days specified. |
|
Allow changing password after (days) |
If selected, users can change the password after it has been in use for the number of days specified. |
|
Password History Count |
This specifies how many old passwords to store. When the user changes password, it must be different than the last password. The password history is only checked when the user changes password by specifying the current password.
|
|
Password Complexity Properties |
Description |
|---|---|
|
Minimum password length |
Enter the required number of characters in a password. |
|
Minimum number of non-alphanumeric chars |
Enter the number of numeric characters or symbols that must be included in the password (in addition to alphabetic characters). Setting this option to 1 is a good idea. |
|
Password strength regular expression |
Optionally, enter the regular expression to be used for enforcing the password's expression. A regular expression is a pattern describing the required format of a password. For help, see the Tip below. |
|
Account Lock on Login Failure Properties |
Description |
|---|---|
|
Lock account after failed login (N attempts) |
If selected, the user account is locked when the Security Server detects the number of failed attempts specified. A locked user account prevents the user from additional log in attempts for a period of time determined by the policy options below. |
|
Reset login attempt after (minutes) |
If selected, enter the number of minutes that must pass between any two log in attempts to ensure that a lockout does not occur. The range is 1 to 999. |
|
Lock account forever (until admin unlocks) |
If selected, when the number of failed logins is reached the account is locked and requires a Security Server administrator to unlock the account. An administrator can unlock the account by going into the user account and deselecting the Account Locked check box; for more information, refer to Security Privileges for Users and Groups. |
|
Lock account for (mins) |
If selected, when the number of failed logins is reached the account is locked and cannot be logged into until this number of minutes go by. |
|
Login Property |
Description |
|---|---|
|
Concurrent Login Limit |
If selected, sets the limit of the number of concurrent log ins. Enter a number in the text entry field or use the up or down arrow buttons. |
|
Logout Properties |
Description |
|---|---|
|
Auto Logout after (mins) |
If the checkbox is selected, the number of minutes before the system automatically logs the user off. The range is 1 to 50,000 minutes. The default is enabled and for 30 minutes. Log out options can be either a Fixed number of minutes or Based on user inactivity. |
|
Auto logout for disconnected clients (sec) |
If selected, sets the number of seconds from the time of client disconnection before the system automatically logs the user off. Enter a number in the text entry field or use the up or down arrow buttons. |
|
Password required to logout |
If selected, users must log out when they have finished using GENESIS64 applications; users must enter the user account password to log out. |
|
|
Tip: Regular Expressions. When using RegEx, the other Settings become irrelevant. For information on regular expression go to this Microsoft web page. The following three examples of regular expressions may be useful to you as a starting point:
|
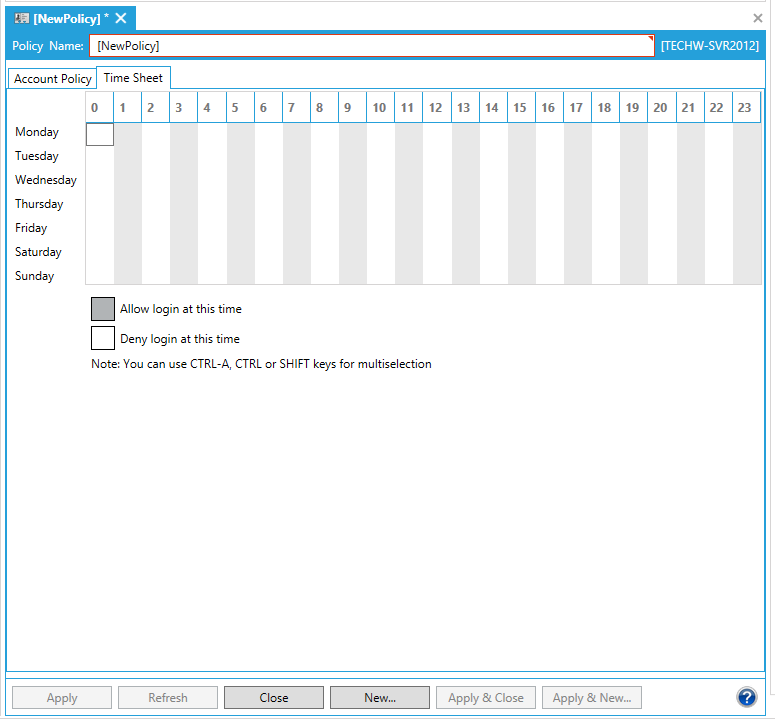
Time Sheet Tab
The Time Sheet tab for account policies lets you restrict application use based on the time of day, on an hourly basis. Access is allowed for hours that are highlighted; access is denied for hours that are not highlighted.
To select a range of time, hold the Shift key then click at the start and end of the range. If you already have a range selected, hold the Shift key and then click on the point that you would like to extend the selected range to. To select uncontiguous areas of the time sheet, hold down the Ctrl key and click on the areas of time you want to select. You can also use Ctrl-A for selecting an entire range of time.
Policy Settings - Time Sheet
See also: