Global Settings
Global Settings allows you to configure settings for security authorization through various security services. Global Settings is accessed through the Security node in Workbench. ![]() View image
View image
Global Settings consists of five tabs: General, Web Login, Critical Points, Critical Alarms, and Authorization. Each tab is described below in this topic.
General Tab
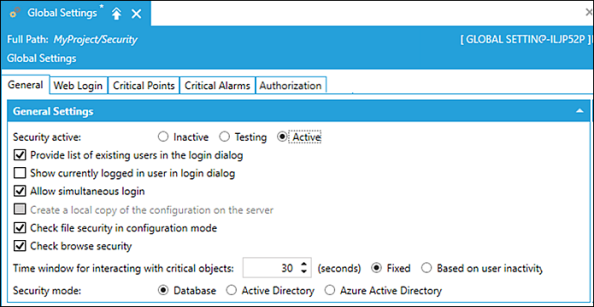
The General tab provides access to the security settings that control how the GENESIS64™ Security server maintains accounts in its database. You can choose to have the Security Server interact with the Windows domain services and provide the connection to the correct domain, how the account username in the ICONICS security database maps to the Windows domain account, and provides the necessary domain credentials so that GENESIS64 can accept pass-through authorization from the Windows domain.
You can set a policy that accepts the current Windows user account credentials, populate the login
dialog with domain users, and change the security mode. Settings maintained
in the security server database are the automatically synchronized with
the domain service. ![]() View image
View image
General Settings:
- Security
active settings:
- Inactive indicates security is deactivated—permissions are granted all the time.
- Testing indicates security is activated, but when nobody is logged in, all permissions are granted. When somebody is logged in, permissions are granted as normal. This setting is mostly meant for the phase when setting up a GENESIS64 installation, as it allows tweaking the settings while minimizing the risks of getting locked out.
- Active indicates security is active as normal.
- Provide list of existing users in the login dialog. When this checkbox is selected, the Security Login dialog box displays a list of all users in the User Name drop-down list. This option is often desirable for touch-screen systems.
- Show currently logged in user in login dialog. When this checkbox is selected, the Security Login dialog box displays the name of the most recent and current user that successfully logged in via the User Name field.
- Provide detailed login error code. The purpose of this checkbox is to notify the user when a login error occurs.
- By default, the checkbox is not selected—a login error displays the generic message, Invalid user name or password.
- When the checkbox is selected, a log-in error condition displays specific error messages:
- invalid username,
- wrong password, or
- user account locked (security is set to Database Security.)
 We recommend that you keep the checkbox clear (unchecked), as exposing the specific error messages is considered a security weakness of the type CWE-200 (common weakness enumeration).
We recommend that you keep the checkbox clear (unchecked), as exposing the specific error messages is considered a security weakness of the type CWE-200 (common weakness enumeration). - Allow simultaneous login
- Create a local copy of the configuration on the server
- Check file security in configuration mode
- Check browse security
- Time window for interacting with critical objects. Amount of time (in seconds) after logging in that a user will be allowed to manipulate a critical point before being required to log in again.
- Security
mode allows you to select one option. Other than the Database option, selection of the Active Directory or Azure Active Directory displays additional settings.
- Database
- Active Directory Allows GENESIS64 Security to connect to a standard Active Directory server.
- Azure Active Directory (also known as Azure AD) Allows GENESIS64 Security to connect to the cloud-based Azure Active Directory (now known as Microsoft Entra ID.)
Active Directory Settings
The Active Directory security mode uses Microsoft's Active Directory over LDAP (Lightweight Directory Access Protocol). If you choose to use the Active Directory synchronization, only one Windows domain can be used to authenticate users. This eliminates the need for users who have already logged in to a Windows domain to enter a username and password a second time to gain access to the security server through the security login. ![]() View image
View image
Active Directory Settings
- Domain Name can be a long or short (NetBIOS) name.
- Server Type options:
- Domain LDAP is where security connects to the default controller of the domain.
- Global Catalog is where security connects to the Global Catalog in Active Directory. This is a read only cache of all domains. This option is used if users are in multiple domains inside a single forest and security needs to show them all.
- Map user name from uses the selected Active Directory attribute as the username (either the SAM-Account-Name or User-Principal-Name). Users who do not have this attribute specified in the Active Directory will not be shown.
- Initial administrator account enables all Application Actions checkboxes for the user and puts an asterisk (*) next to the user's security permission after selecting the Apply button. Note that you cannot use a group account for this setting.
-
AD synchronization period is set to 60 minutes. The period you specify is aligned to UTC time, which means that it is set to 24 hours. For example, the synchronization will happen at UTC midnight.
Click Synchronize now to perform a full synchronization of Active Directory users and groups on the default FrameWorX™ server. The result (success or failure description) is shown next to the button. The task to resynchronize the Active Directory is exposed as a Point Manager Method with the name ?\FullSyncExternalSecurityProvider, which makes it possible to execute it through a command.
To execute the Point Manager Method on the default FrameWorX server, you need to have permission to execute the application action Workbench/Security/Edit Items. The permissions on the Methods tab are ignored.
To execute this Method on a remote FrameWorX server, the behavior is opposite (permissions on the Methods tab are ignored). To execute this method on a remote FrameWorX server, the behavior is opposite (permissions on the Methods tab get applied while the application action permissions are not checked for the end user that executes the method).
-
User authentication method is a drop-down list to select Active Directory, Active Directory (User-Principal-Name being translated to SAM-Account-Name), Active Directory (SAM-Account-Name being translated to User-Principal Name), or Local Logon.
Important about Local Log on Authentication: Instead of connecting to the Active Directory directly using the credentials of the user that is logging into GENESIS64™ (the default method), this method does so through the local system function called LogonUser. This has the advantage that the system caches the user’s credentials once he successfully logs in, and later, when the Active Directory is not available, a user with cached credentials can still log in. This method comes with disadvantages as well, though:
- The server computer must be joined to the Active Directory domain.
- The user must be allowed to log on to the server computer.
- This method will not work if the domain name setting in Global Settings contains the name of an actual domain controller. It must only contain the domain name.
- Caching does not seem to work when the usernames are in the user principal name form (user@domain.com)
- The use of the Local Log on method, together with caching behavior, makes it possible for users to log into GENESIS64 Security even when the Active Directory is currently not reachable. But Active Directory still needs to be available during FrameWorX™ Server start up, so that its structure can be cached.
- Show Managed Service Accounts: Select this checkbox to show the managed service accounts.
Automatic log in allows you to indicate the following:
- Enabled: Select this checkbox to
enable automatic log in.
 For the automatic log in to work, it is necessary to set the Client Authentication option to 'Integrated Windows Authentication' in the FrameWorX™ Server
Location dialog settings under the Tools menu, or to set up authentication
using client certificates that map to Active Directory.
For the automatic log in to work, it is necessary to set the Client Authentication option to 'Integrated Windows Authentication' in the FrameWorX™ Server
Location dialog settings under the Tools menu, or to set up authentication
using client certificates that map to Active Directory. - Also enable manual login: Select this checkbox to allow manual login in addition to automatic.
- Allow the automatically logged in user to log out: Select this checkbox to allow a user who may have automatically logged in to also have the ability to log out.
Only users from a specific group allows you to indicate the following:
- Enabled. Select the checkbox to allow log in only from a named group. Once checked, you can enter the group name.
- Group name. Enter a group name in the text entry field that will contain users allowed to log in.
- Show groups of every user. Select the checkbox to show each user that's related to groups.
Domain connection authentication is used to secure the connection between our Security (running as an internal part of the FrameWorX Server) and the Active Directory.
- Username and Password authenticate access to the Active Directory, so that Workbench and security can list users and groups. If information is not entered, security tries to authenticate using the identity of the FrameWorX server process—this authentication only works if the FrameWorX server process is running under a domain account that has access to the Active Directory.
- Authentication type defines how credentials are transferred to Active Directory for verification. Select the appropriate option—Secure or Basic (simple bind) authentication. These two setting correspond to the options “Secure” and “None” in this link: https://msdn.microsoft.com/en-us/library/system.directoryservices.authenticationtypes.aspx.
Use Secure Sockets Layer (SSL). Security uses LDAPS (LDAP over SSL). This needs to be supported by the Active Directory. Details regarding this set up are outside our concern.
 ICONICS Suite™ (GENESIS64™,
Hyper Historian™, AnalytiX®, MobileHMI™) is compatible with Azure Active
Directory Domain Services. Users should be able to synchronize ICONICS
security with an Azure AD tenant that has been integrated with Azure Active
Directory Domain Services. auto-login should work as well, provided that
all machines are joined to the domain.
ICONICS Suite™ (GENESIS64™,
Hyper Historian™, AnalytiX®, MobileHMI™) is compatible with Azure Active
Directory Domain Services. Users should be able to synchronize ICONICS
security with an Azure AD tenant that has been integrated with Azure Active
Directory Domain Services. auto-login should work as well, provided that
all machines are joined to the domain.See this link for more information on how to configure Azure Active Directory Domain Services: https://docs.microsoft.com/en-us/azure/active-directory-domain-services/active-directory-ds-getting-started
Azure Active Directory

Azure Active Directory Settings
- Application (client) ID: Enter the Application (client) ID in the text entry field.
- Directory (tenant) ID: Enter the Directory (tenant) ID in the text entry field.
- Client secret: Click the ellipsis button [...] to open the 'Shared secret' window and enter the Secret in the text entry field. Close the box to save your Secret.
- Initial administrator account: Enter the initial administrator account in the text entry field.
- AD synchronization period: Enter an Active Directory synchronization period, in minutes, in the text box. Click the Synchronize now button to call the method ?\FullSyncExternalSecurityProvider on the default server to perform a full synchronization of Active Directory users and groups.
Automatic log in
- Enabled: Select the checkbox to
enable automatic log in.
 For automatic login to work, it is also necessary to enable to the
option "Use Integrated Windows Authentication" in the Default Server
Location dialog settings under the Tools menu, or to set up authentication
using client certificates that map to Active Directory.
For automatic login to work, it is also necessary to enable to the
option "Use Integrated Windows Authentication" in the Default Server
Location dialog settings under the Tools menu, or to set up authentication
using client certificates that map to Active Directory. - Also enable manual login: Click this checkbox to allow manual log in in addition to automatic.
- Allow the automatically logged in user
to log out: Click this checkbox to allow a user who may have
automatically logged in to also be able to log out.
 If this checkbox is
not selected, Web Login is unable to log anybody in through
the Web when there is already somebody logged in automatically.
If this checkbox is
not selected, Web Login is unable to log anybody in through
the Web when there is already somebody logged in automatically.
Only users from a specific group
- Enabled: Select the checkbox to allow log in only from a named group. When checked, you can enter the group name in the setting below.
- Group name: Enter a group name in the text entry field that will contain users allowed to log in.
Web Login Tab
Web Login allows an OIDC, SAML 2.0 IdP, or Azure Active Directory to connect and authenticate client access to the GENESIS64™ applications. Two key features that the Web Login are:
- The security component inside FrameWorX™ Server acts as an OpenID Connect (OIDC) IdP that other clients can connect to and authenticate.
- Security can connect to a third-party OIDC or a SAML 2.0 IdP and outsource the authentication to them.
These two features can be combined, where a client can connect to the OIDC IdP exposed by ICONICS security to obtain an OIDC token, and the security redirects the client to an external SAML or OIDC IdP to perform authentication.
 If you see this error (Authentication failed error: "Could not complete OAuth 2.0 token request"), you must generate a new certificate for the OIDC token signing.
If you see this error (Authentication failed error: "Could not complete OAuth 2.0 token request"), you must generate a new certificate for the OIDC token signing.
To generate a new certificate, open PowerShell and run this script: & “C:\ProgramData\ICONICS\Set-CertificatePermissions.ps1” “certificate subject name”. For example, you could type the following: & “C:\ProgramData\ICONICS\Set-CertificatePermissions.ps1” “FrameWorXServer”. The script is digitally signed and timestamped by ICONICS, so you will only be asked to trust this publisher once.
This section setup security for an external IdP, as well as configure the external IdP login.
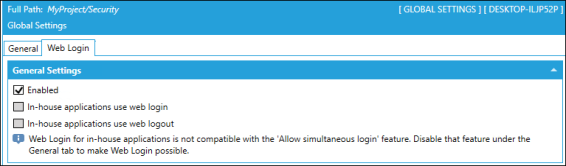
- Enabled. Select the checkbox to enable the ODIC IdP and external IdP functionality for security. Otherwise, the OIDC/OAuth HTTP endpoints remain functional, although they will not allow any authorization.
- In-house
applications use web login.
Select this checkbox when connecting an external IdP. This instructs the GENESIS64™ applications, such as GraphWorX™64 or Workbench, to allow web browser user login instead of the regular login dialog.
 In-house applications use web login. You cannot select this option when the Allow simultaneous
login checkbox is selected (enabled) in the General Settings section on the General tab. You need to clear the checkbox on the General tab.
In-house applications use web login. You cannot select this option when the Allow simultaneous
login checkbox is selected (enabled) in the General Settings section on the General tab. You need to clear the checkbox on the General tab.Additionally, Web Login in comes with some limitations:
- When using Integrated Windows Authentication to automatically log users into GENESIS64, it is advisable to automatically log out the user. This is a Global Settings option . If this option is not selected, Web Login is unable to log anybody in through the web if there is somebody already logged in automatically.
- The policy Password required to log out is ignored for users that logged in through Web Login.
- The Global Settings options Critical Points and Critical Alarms will not work. These points and alarms will always be inaccessible for users logged in through the Web Login.
In-house applications use web logout. Selecting this checkbox instructs GENESIS64™ applications, such as GraphWorX™64 or Workbench, to log out the user and
 initiate a single logout (SLO) for external IdPs (either SAML 2.0 or ODIC providers).
initiate a single logout (SLO) for external IdPs (either SAML 2.0 or ODIC providers). When the user clicks the Logout button, the web logout process begins. Other logout events, such as automatic logout due to inactivity or an automatic logout when all clients disconnect, do not initiate a web logout. Additionally, when security is connected to an external SAML provider, then this checkbox enables an IdP-initiated logout.
 Select (enable) the In-house
applications use web login checkbox first to allow the web logout function.
Select (enable) the In-house
applications use web login checkbox first to allow the web logout function.
OIDC Provider / OAuth Authorization Server Settings Section
This section sets up the OIDC provider (called ‘Authorization Server’ in OAuth terminology) that is built into security.

- Issuer URL. Identifies the base URL endpoints where Security listens on. This URL cannot be changed directly—it serves just to inform you about the URL. To change the base address where Security listens on. see Changing the URL that Security Listens To and Enabling HTTPS (accessed from the Workbench Tools tab.)
Signing credentials type. Designates what certificate to use to cryptographically sign the OIDC/OAuth tokens.
Auto-generated temporary key should only be used for testing. Security will generate a new random key every time it starts, so all clients that are already authenticated will lose the authentication and will need to authenticate again.
From the windows certificate store selects a key saved in the certificate store. For OIDC/OAuth, the certificate does not need to be signed by a trusted authority.
- Select certificate by. Selects a certificate from the certificate store.
- Certificate identifier. Enter a certificate
identifier or select the tag button
 which opens the
Windows Security window based on your signing credentials selection (above). All certificates used by the GENESIS64 back end should be stored in the computer certificate store.
which opens the
Windows Security window based on your signing credentials selection (above). All certificates used by the GENESIS64 back end should be stored in the computer certificate store.

- Allowed CORS origins. An optional
new line-separated list of JavaScript client origins allows
the use of the OIDC/OAuth feature to log in. This is only required
for JavaScript SPAs (Single page applications) and only if hosted on a different domain from the FrameWorX Server. Currently,
in GENESIS™64 V10.96 applications, ICONICS does not have any such in-house
applications, so this only applies to custom-developed SPAs.
 CORS origins are case-sensitive.
CORS origins are case-sensitive. - In-house application Relying Party Redirect URIs. These are the OIDC Redirect URLs used by GENESIS64 applications (GraphWorX64). Normally, there should be no need to change these. The {host} placeholder gets replaced by the server name. See Changing the URL that Security Listens to and Enabling HTTPS on what name that will be.
- In-house application Relying Party post logout Redirect URIs. These are the OIDC Post Logout Redirect URLs used by GENESIS64 applications. Normally, there should be no need to change these. The {host} placeholder gets replaced by the server name.
Authentication Section
The Type drop down menu allows you to select the authentication protocols. Addition information is displayed based on the selection.
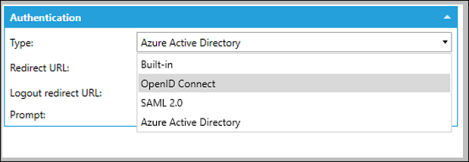
- Built-in is the default option. Security presents its own login page that authenticates against
either Active Directory or against the list of users or groups. The following setting appears with this selection:
- Allow the 'Remember me' option in the web login form checkbox, when selected, enables an authentication cookie in the user’s web browser, so the next time the browser is opened and the OIDC/OAuth log-in feature is used, the user will already be signed in. If this checkbox is not selected, the cookie remains in the user’s web browser only until the browser session ends.
- OpenID Connect option, together with
the OIDC Authentication User Mapping section, set up login authorization through an
external OIDC IdP. The following settings appear with this selection:
- Redirect URL This value is informational only and will be required when setting up the external OIDC identity provider.
Logout redirect URL This value is informational only and will be required when setting up the external OIDC identity provider.
 For
information about changing the base URL, See the section
Changing the URL that Security Listens
To and Enabling HTTPS.
For
information about changing the base URL, See the section
Changing the URL that Security Listens
To and Enabling HTTPS.- Issuer URL is the base URL of the endpoints of the external OIDC provider. Enter the Issuer URL for authentication in the text box.
- Client ID is the OIDC/OAuth client identifier. Enter the client ID associated with the issuer URL/authentication in the text box.
- Client secret (if required) is stored in the database in obfuscated form and can be reverted to clear text easily. Enter the client secret used for the external authentication in the text box or click the ellipsis button [...] to open the Shared secret window, where you can enter the secret.
- Use PKCE to determine whether the client must use PKCE (Proof Key for Code Exchange).
- Prompt is an optional OIDC protocol parameter that instructs the OIDC identity provider to re-prompt the user for some information. See this link for more information: https://openid.net/specs/openid-connect-core-1_0.html#AuthRequest. Select the appropriate checkbox (Default, Login, Consent, or Select account) for the authentication prompt.
SAML 2.0 See SAML 2.0 Authentication settings.
Azure Active Directory Uses the OIDC protocol, but instead of setting all the details, this takes the details from the Azure Active Directory Settings section of the General tab. This authentication uses the Microsoft identity platform: https://learn.microsoft.com/en-us/entra/identity-platform/v2-overview.
Specifically, these settings are used:
- The Authorization Code flow is used.
- The issuer URL is formatted as https://login.microsoftonline.com/{tenant}/v2.0.
- The 'profile' scope gets requested.
- The 'oid' claim from the ID token gets extracted and mapped to the ID property read from Azure Active Directory.
OIDC Authentication User Mapping
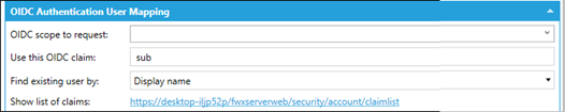
- OIDC scope to request. By default, Security requests only the ‘openid’ scope. It is possible to specify additional scopes here (even multiple, space delimited). The combination box option contains the standard scopes defined by the OIDC standard, but identity providers can define their own. Use the drop-down list to select from profile, email, address, or phone.
- Use this OIDC claim. What claim to extract from the OIDC tokens when mapping to existing users. Servers are likely to define their own claims, but a list of standard ones can be found here: https://openid.net/specs/openid-connect-core-1_0.html#StandardClaims. Enter an OIDC claim to use for user mapping with external authentication. This field may be pre-populated but can be edited.
- Find existing user by. Use the menu to select from Display Name, Unique name (Active Directory GUID), Active Directory SID (Security ID), or Active Directory UPN (User Principal Name).
- Show list of claims. The Show list of claims hyperlink opens a web page that redirects to the external IdP and then lists all the claims that it extracted from the token. To use this link, you need to click Apply and wait a second for the server to notice the changes and reconfigure.
SAML 2.0 See SAML 2.0 Configuration Settings.
Critical Points Tab
On the Global Settings Critical Points tab, you can designate a subset of writable points (OPC data items) known as critical points. When writing a new value to a critical point, the user is prompted to log in again immediately before writing a new value. This ensures that the person writing the value is an authenticated user.
 Do not configure a point to be both an extra authentication point and a critical point. They are not intended to be used together.
Do not configure a point to be both an extra authentication point and a critical point. They are not intended to be used together.
You can use wild cards as part of the point name. This lets you specify multiple tags without listing them individually. For details about how to do this, refer to Wildcards and Performance Optimization.
For a user to write a new value to a critical point, two conditions must be met:
- The user must be granted rights to the point via his or her user configuration or through one of the explicit groups he or she belongs to. (Rights cannot be granted from the default group).
- The user must have logged in within the past Time window for interacting with critical objects period (configured on the Global Settings Policy tab). If condition 1 is met, but not condition 2, the client application, such as GraphWorX™64, opens a security login dialog, requiring the user to log in again to satisfy condition 2.
Critical Alarms Tab
On the Critical Alarms tab of Global Settings, shown in the figure below, you can designate a set of critical alarms. When writing a new value to a critical alarm, the user will be prompted to log in before acknowledging an alarm. This ensures that the person acknowledging the alarm is an authenticated user.
You can use wild cards as part of the point name. This lets you specify multiple tags without listing them individually. For details about how to do this, refer to Wildcards and Performance Optimization.

Authorization
The Authorization tab adds an extra layer of security on top of standard security, requiring single or double authentication to comply with FDA e-signature requirements.
The administrator or other authorized persons define all data sources and process points requiring security and authorization and then designates the authorization level by assigning the Performer and Verifier roles.
- For single authentication, only the Performer role checkbox must be selected.
For double authentication, both the Performer and Verifier checkboxes must be selected.
 A person can hold the Performer and Verifier role but cannot fulfill both roles for the same operation.
A person can hold the Performer and Verifier role but cannot fulfill both roles for the same operation.
For example, the Performer uses a single authorization for Building B operations without getting additional permission from the Verifier. Whereas, for Building A operations, the Performer requires additional verification and approval from the person assigned to the Verifier role who either allows or denies access.

 You should not configure a point to be both an extra authentication point and a critical point. They are not intended to be used together.
You should not configure a point to be both an extra authentication point and a critical point. They are not intended to be used together.
The Authorization tab also appears on the Security Groups and User nodes—this defines what a user or group of users can and cannot do, such as granting or restricting access to information in GraphWorX™64. See Security Privileges for Users and Groups and Password Authorization in GraphWorX64
See also: