Security Privileges for Users and Groups
Security options for user and groups are defined by the administrator or authorized personnel. You can apply security restrictions at the group level, the user level, or both. The following are security rules for determining whether a privilege is extended or denied to a user:
- If a user lacks a privilege and is added to a group, the group privileges are extended to that user.
- Least restrictive permissions take precedence. One exception is that a user and group can be denied access to an application action or a defined data point. Deny takes precedence over Allow.
Once a group or user account is defined, you
define its application privileges for the group and user.
 Privileges can be extended or denied to users and groups
on an application-by-application basis. The Application
Actions section
is where you define the privileges for a User or for a Group.
Each client application has its own set of actions that you have precise control over. See Users and Groups for addition information.
Privileges can be extended or denied to users and groups
on an application-by-application basis. The Application
Actions section
is where you define the privileges for a User or for a Group.
Each client application has its own set of actions that you have precise control over. See Users and Groups for addition information.
Granting and Denying Access
Each of the following tabs contain Allow these operations and Deny these operations sections. Click + to enter the string. During run-time, theGENESIS64 client sends an point string for access testing (granted or denied). The include and exclude lists are string-compared as described below for each active user and group until access is granted. OPC point strings are used in this example, but the same logic applies to all objects that require access:
- Compare the OPC point string with each string in the include list until a match is found. If no match is found, access is denied.
- If a match is found in the include list, compare the OPC point string with every string in the exclude list. If no match is found in the exclude list, access to the point is granted, and no further testing of active groups and users is performed.
About Tabs
-
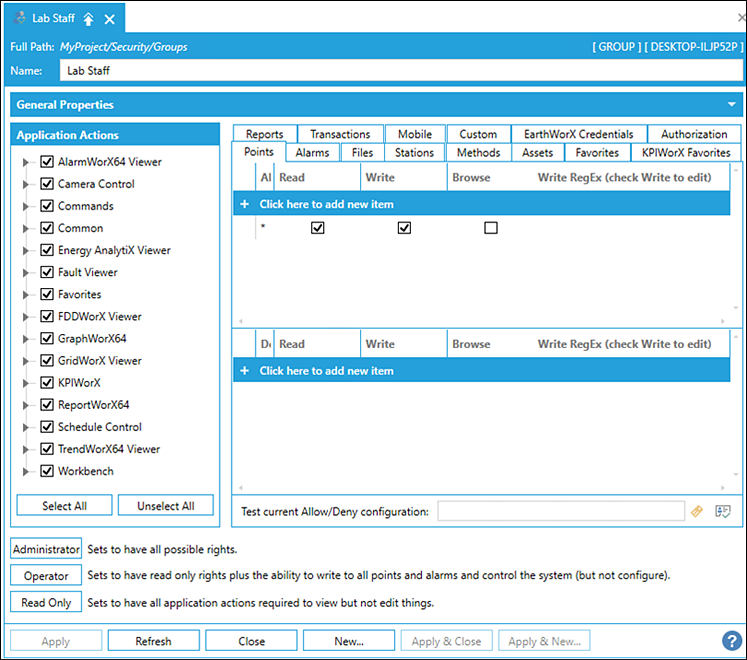
 Points
tab
Points
tab
If an GENESIS64 application is configured to write to points in OPC server and other data sources will get disabled if denied by the security server. Point names (with or without wild cards) are placed in include or exclude lists for each user or group.
 You should not configure a point to be both an extra authentication point and a critical point. They are not intended to be used together.
You should not configure a point to be both an extra authentication point and a critical point. They are not intended to be used together.The Points tab is used secure recipes and identifies what recipe items are allowed or denied for an individual user or group of users. See Recipe Security.
Before a GENESIS64 client writes a process value to a server, the unique string (the point name) identifies the output point being sent to the security server to determine if the write function is allowed based on the currently logged-in users and/or the groups permissions. Use the Points tab to configure which output points are allowed or denied for users and groups (see Granting or Denying Access). Refer to Wildcards and Performance Optimization for a description of the wild cards you can use.
Folders can also be hidden based on security. Folder names can be added to a user or group's Points tab, and the Browse checkbox can be used to allow or deny visibility of that folder in the Data Browser.
Users can select a folder in the Data Browser and view the breadcrumb bar to see the name of the folder according to security. Wild cards can be used in this name as normal when adding it to the Points tab in security.
 Some data providers do not have hierarchical
names for folders. These providers may be unable to hide and show individual
folders with security.
Some data providers do not have hierarchical
names for folders. These providers may be unable to hide and show individual
folders with security. -
 Alarms tab
Alarms tab
The Alarms tab controls access to alarm acknowledgment during runtime. You can protect individual alarms or groups of alarms by securing those alarms. Do so by placing alarm names with or without wildcards include (allow acknowledgment) or exclude (deny acknowledgment) lists for each user or group. (Include and exclude lists are commonly used by file backup programs to specify a backup set.) Application queries the Security Server for alarm access before opening a file. Refer to Granting or Denying Access for a description of how entries on this tab are used. Refer to Wildcards and Performance Optimization for a description of the wild cards you can use.
Alarms can also be secured by asset name. See Secure Alarms by Asset Name for more information.
-
 Files tab
Files tab
The Files form controls access to files that GENESIS64 clients may open during runtime. You can use any of the features that are available, but all are optional and should be used only in accordance with policy strategies you have set up at your company. This tab is frequently used to define user access to GraphWorX64 display files; some users create the files and need complete access to the files they create, while others are runtime users such as dashboard operators or supervisors who much monitor operations.
In the Allow These Operations section, identify the files that the user can access then select the actions that are allowed for each file. In the Deny These Operations section, identify the files and actions that users are specifically denied. In both sections, you can use wild cards to include multiple files with one entry.
Refer to Granting or Denying Access for a description of how entries on this tab are used. Refer to Wildcards and Performance Optimization for a description of the wild cards you can use. The runtime processing and wildcard pattern matching apply here with the following differences:
- The pattern matching is done on the file extension, separate from the file name, to match the DOS wildcard semantics. For example, the wildcard string to indicate all files is *.*
- You must specify the file path (or include * before the filename).
-
 Stations tab
Stations tab
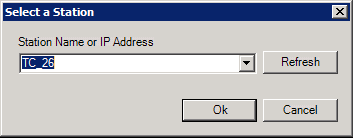
The Stations form is used to grant (allow login) or restrict (deny login) access from specific nodes on the network. Each node on a Microsoft network is identified by a unique computer name. Refer to Granting or Denying Access for a description of how entries on this tab are used.
When you click the Ellipsis button [...], the Select a Station dialog box appears, as shown in the figure below. Select the Station Name from the drop-down list, or enter the name or system IP address into the drop-down list box to define the station criteria.
-
 Methods tab
Methods tab
The Methods tab is used to grant or restrict the use of listed methods.
-
 Assets tab
Assets tab
The Assets tab is used to grant or restrict the visualization and / or execution of listed assets in a connected asset catalog database through the AssetWorX™ provider in the Workbench. See Securing Individual Equipment Commands.
-
 Favorites tab
Favorites tab
The Favorites tab is used to grant or restrict the visualization and/or execution of favorite operations.
-
 KPIWorX
Favorites tab
KPIWorX
Favorites tab
The KPIWorX Favorites tab is used to grant or restrict the visualization and / or execution of KPIWorX Favorite operations. Identify the root folder and designate if the user or group can see or modify information.
-
 Reports tab
Reports tab
The Reports tab is used to grant or restrict the download, execution, and / or approval of reports
-
 Transactions
tab
Transactions
tab
The Transactions tab is used to grant or restrict the download and / or execution of transactions.
-
 Mobile
tab
Mobile
tab
The Mobile tab is used to grant or restrict the visualization (to read or modify) of listed mobile operations.
-
 Custom
(Strings) tab
Custom
(Strings) tab
VBA scripts may use custom-defined strings as security tokens that are evaluated by the Security Server. As with the file names, custom strings with or without wildcards are placed in include (allow access) or exclude (deny access) lists for each user or group. The Custom form, shown below, is used to include or exclude strings that will be tested in runtime by VBA scripts executing within clients. The meaning of these strings and the functionality they protect are controlled entirely by the author of the VBA script.
Refer to Wildcards and Performance Optimization for a description of the wild cards you can use. Refer to Granting or Denying Access for a description of how entries on this tab are used. For example, from a GENESIS64 VBA script, a custom security item is tested by calling the method TestCustomSecurityItem(BSTR in the GwxDisplay object.
-
 EarthWorX
Credentials tab
EarthWorX
Credentials tab
The EarthWorX Credentials tab is used to grant or restrict visualization and / or execution options within the EarthWorX provider.
-
 Authorization tab
Authorization tab
The Authorization tab defines the security permissions needed to access GENESIS64 applications, adding another layer of security on top of the ICONICS standard security. Authorization uses the Performer and Verifier roles that are assigned to individual users or a group of users. For example, the performer uses a single sign-on without getting additional permission from the verifier. If the performer views or changes a process or value that requires additional verification, the person assigned to the verifier role allows or denies access.
 You should not configure a point to be both an extra authentication point and a critical point. They are not intended to be used together.
You should not configure a point to be both an extra authentication point and a critical point. They are not intended to be used together.Global Settings - Authentication Tab defines all the data sources or data points requiring authorization. Individual Users and Groups are assigned roles as Performer and Verifier. A person can hold the Performer and Verifier role but cannot fulfill both roles for the same operation.
Security authorization includes password authentication in GraphWorX64™ including access to recipes in the application. See Password Authorization in GraphWorX64.
Securing Individual Equipment Commands
The Assets tab of a Security User or Security Group setting can separately allow or disallow the use of individual commands defined on equipment in AssetWorX™. This is controlled by the Execute checkbox and the command name in the text field.
While the browse button helps with setting up the correct syntax for the text field, here are a few examples to explain the logic. The first three columns of the table correspond to settings in the Assets tab on either the User or Group setting.
 The correct syntax must
be set up manually.
The correct syntax must
be set up manually.
|
Allow view or ack these alarms |
Execute |
Visualize |
Description |
|---|---|---|---|
|
ac:Equipment/|CmdName=MyCommand |
☑ |
☐ |
The Asset Navigator just shows the command named MyCommand on ac:Equipment/
|
|
ac:Equipment/|CmdName=MyCommand |
☑ |
☑ |
The same as the previous row. The Visualize checkbox has no effect at all because the text field specifies a command |
|
*|CmdName=MyCommand |
☑ |
☑ |
Allows the MyCommand command on all Equipment. Again, the Visualize checkbox has no effect. |
|
ac:Equipment/ |
☑ |
☐ |
As no command name is specified, this allows all commands on the equipment ac:Equipment/. |
See Also:
Displaying Current Logged-In User Information