Global Settings (Web Login)
[For more info on Web Login, click HERE.]
To Edit the Global Settings (Web Login) Properties:
-
Expand your project in the Workbench's Project Explorer, then expand the Security provider node, and then the Web Login sub-node.
-
Double-click on the Global Settings node, or right-click on the Global Settings node and select Edit from the menu, or select the Global Settings mode then click on the Edit button in the Edit section of the Home ribbon in the Workbench.
-
This opens the Global Settings properties, shown below.
Global Settings (Web Login) Properties
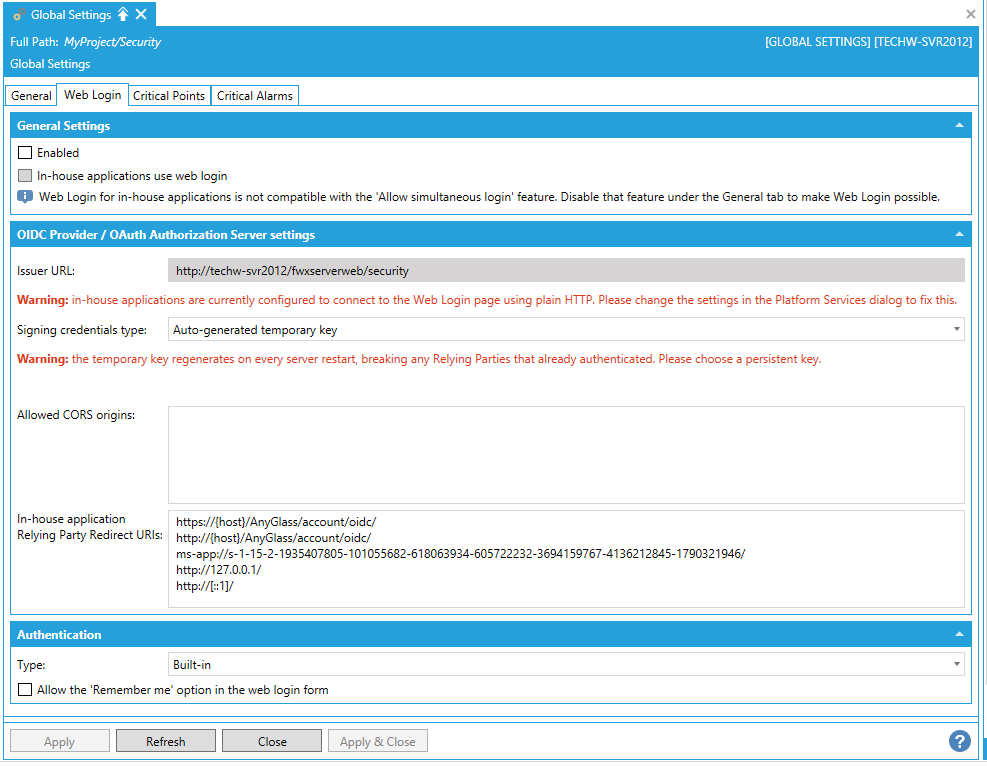
General Settings
These settings set up both Security as an OIDC IdP, as well as configure the external OIDC or SAML login.
-
Enabled -Enables the OIDC IdP. When disabled, the HTTP endpoints of OIDC/OAuth remain functional, although they will not allow any authentication/authorization. Click the checkbox to enable the selected OIDC Provider.
-
In-house applications use web login -This instructs the GENESIS64 applications to use Web Login, instead of the regular Login dialog. This option only make sense when also using some sort of external IdP. If not, using the regular Login dialog is the preferred way to authenticate.
-
Web applications use web login -This instructs the web applications to use Web Login, instead of the regular Login dialog. This option only make sense when also using some sort of external IdP. If not, using the regular Login dialog is the preferred way to authenticate.
Note: Web Login in those applications also comes with limitations.
-
The Allow simultaneous login must be disabled on the General tab of Global Settings.
-
When logging into GENESIS64 using Integrated Windows Authentication to automatically log in users, it is advisable to also allow to log off the automatic user. This is an option on the Global Settings. If this option is left disabled, Web Login will not be able to log anybody in through the Web if there is already somebody logged in automatically.
-
The 'Password required to log out' Policy is ignored for users that logged in through the Web Login.
-
The Critical Points and Critical Alarms will not work. These points and alarms will always be inaccessible for users logged in through the Web Login.
OIDC Provider / OAuth Authorization Server Settings
This section sets up the OIDC Provider (called ‘Authorization Server’ in OAuth terminology) that is built into Security.
-
Issuer URL -The base URL of the OIDC/OAuth endpoints. This field cannot be changed directly, it serves just to inform about the URL. To change the base address where Security listens on, see the separate section ‘Changing the URL that Security Listens On and Enabling HTTPS’.
-
Signing credentials type -What certificate to use to cryptographically sign the OIDC/OAuth tokens. Use the pulldown menu to select either 'Auto-generated temporary key' or 'From the windows certificate store'. Your selection will determine whether you can make further edits to the General Settings properties.
-
Auto-generated temporary key – This option should only be used for testing. Security will generate a new random key every time it starts, so all clients that already authenticated will lose the authentication and will need to re-authenticate again.
-
From the windows certificate store – Selects a key saved in the certificate store. For OIDC/OAuth, the certificate does not need to be signed by a trusted authority.
-
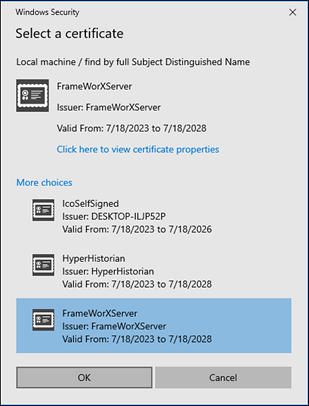
Select certificate by/Certificate identifier - Serves to select a certificate from the certificate store. If you selected 'From the windows certificate store' as your selected Signing credentials type, you can use the now activated pulldown menu to select from 'Local machine/find by Subject Distinguished Name', 'Local machine/find by Thumbprint', 'Current user/find by Subject Distinguished Name'. or 'Current user/find by Thumbprint'. You can enter a Certificate identifier in the text entry field or click on the
 button, which opens the
Windows Security window specific
to what you selected for 'Select certificate by', as shown below.
button, which opens the
Windows Security window specific
to what you selected for 'Select certificate by', as shown below.
Windows Security Window Customized to Selection of 'Local machine/find by Subject Distinguished Name'
-
Allowed CORS origins -An optional new line separated list of JavaScript client origins that are allowed to use the OIDC/OAuth feature for logging in. This is only required for JavaScript SPAs (Single page applications) and only if they are hosted on a different domain than the FrameWorX Server. Currently, in GENESIS64 V10.96 applications, ICONICS does not have any such in-house applications, so this only appies to custom-developed SPAs. Note: CORS origins are case-sensitive.
-
In-house application Relying Party Redirect URIs -These are the OIDC Redirect URLs used by GENESIS64 applications (GraphWorX64, AnyGlass, UWP). Normally, there should be no need to change these. The {host} placeholder gets replaced by the server name. See the section ‘Changing the URL that Security Listens On and Enabling HTTPS’ on what name that will be.
Authentication Section
The Type drop down list allows you to select the authentication protocols. Addition information is displayed based on the selection.
Built-in
With this option, Security will not redirect to an external OIDC or SAML web page, but instead will present its own login page that authenticates against either Active Directory or against the list of users specified directly in Security. There is just one setting for this option.
- Allow the 'Remember me' option in the web login form -This enables or disables a “Remember me” check box on the web login form. When enabled and the user checks the check box, the authentication cookie will be persisted in the user’s web browser, so the next time the browser is opened and the OIDC/OAuth login feature is used, the user will already be signed in. Without this check box checked, the cookie will remain in the user’s web browser only until the browser session ends.
OpenID Connect
These settings, together with the OIDC Authentication User Mapping section, set up login through an external OIDC Identity Provider.
- Redirect URL -This value is informational only and will be required when setting up the external OIDC Identity Provider. For information about changing the base URL, see the separate section ‘Changing the URL that Security Listens On and Enabling HTTPS’.
- Logout redirect URL -This value is informational only and will be required when setting up the external OIDC Identity Provider. For information about changing the base URL, see the separate section ‘Changing the URL that Security Listens On and Enabling HTTPS’.
- Issuer URL -The base URL of the endpoints of the external OIDC Provider. Enter the Issuer URL for authentication in the text entry field.
- Client ID -The OIDC/OAuth ‘Client identifier’. Enter the client ID associated with the issuer URL/authentication in the text entry field.
- Client secret -The client secret, if required. It is stored in the database in obfuscated form and can be reverted to clear text easily. Enter the Client secret used for the external authentication in the text entry field or click on the ellipsis button [...] to open the Shared secret window, where you can type in the secret.
- Use PKCE -Determines whether the client must use PKCE (Proof Key for Code Exchange).
- Prompt -This is an optional OIDC protocol parameter that instructs the OIDC Identity Provider to re-prompt the user for some information. See this link for more information: https://openid.net/specs/openid-connect-core-1_0.html#AuthRequest. Select whether the authentication prompt (Default, Login, Consent or Select account).
SAML 2.0
These settings set up login through an external SAML identity provider. Learn more
Azure Active Directory
This setting is only available when Security is connecting to Azure Active Directory. This uses the OIDC protocol, but instead of requiring to set up all the details, this takes the details from the Azure Active Directory Settings section of the General tab. This authentication uses the Microsoft identity platform: https://learn.microsoft.com/en-us/entra/identity-platform/v2-overview.
Specifically, these settings are used:
- The Authorization Code flow is used.
- The issuer URL is formatted as https://login.microsoftonline.com/{tenant}/v2.0.
- The ‘profile’ scope gets requested.
- The ‘oid’ claim from the ID token gets extracted and mapped to the ID property read from Azure Active Directory.
OIDC Authentication User Mapping
- OIDC scope to request - By default, Security requests only the ‘openid’ scope. It is possible to specify additional scopes here (even multiple, space delimited). The combo box option contains the standard scopes defined by the OIDC standard, but Identity Providers can define their own. Use the pulldown menu to select from profile, email, address, or phone.
- Use this OIDC claim - What claim to extract from the OIDC tokens when mapping to existing users. Servers are likely to define their own claims, but a list of standard ones can be found here: https://openid.net/specs/openid-connect-core-1_0.html#StandardClaims. Enter an OIDC claim to use for user mapping with the external authentication. This field may be pre-populated but can be edited.
- Find existing user by - Use the drop-down list to select from Display Name, Unique name (Active Directory GUID), Active Directory SID (Security ID), or Active Directory UPN (User Principal Name).
See Also: